
Research Article
Substantial Overall Performance Pattern-matching Algorithm for Network Stability
Shoban Babu Sriramoju
Int. J. Res. Appl.(Volume – 5, Issue – 17, Page No’s: 701-704)
DOI:https://zenodo.org/records/13348198
Received: 15th Jan, 2018; Accepted: 07th Feb, 2018; Published: 25th Mar, 2018
Abstract | Full Paper
Substantial Overall Performance Pattern-matching Algorithm for Network Stability
Shoban Babu Sriramoju
Int. J. Res. Appl.(Volume – 5, Issue – 17, Page No’s: 701-704)
DOI:https://zenodo.org/records/13348198
Received: 15th Jan, 2018; Accepted: 07th Feb, 2018; Published: 25th Mar, 2018
Abstract | Full Paper
Case Study
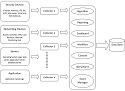
A Study on Security Information and Event Management (SIEM)
Sugandhi Maheshwaram
Int. J. Res. Appl.(Volume – 5, Issue – 17, Page No’s: 705-708)
DOI:https://zenodo.org/records/13348222
Received: 15th Jan, 2018; Accepted: 07th Feb, 2018; Published: 25th Mar, 2018
Abstract | Full Paper
A Study on Security Information and Event Management (SIEM)
Sugandhi Maheshwaram
Int. J. Res. Appl.(Volume – 5, Issue – 17, Page No’s: 705-708)
DOI:https://zenodo.org/records/13348222
Received: 15th Jan, 2018; Accepted: 07th Feb, 2018; Published: 25th Mar, 2018
Abstract | Full Paper
Case Study
A Study on the cycle of Big Data Mining
Pushpavathi Mannava
Int. J. Res. Appl.(Volume – 5, Issue – 17, Page No’s: 709-713)
DOI:https://zenodo.org/records/13348264
Received: 17th Jan, 2018; Accepted: 15th Feb, 2018; Published: 26th Mar, 2018
Abstract | Full Paper
A Study on the cycle of Big Data Mining
Pushpavathi Mannava
Int. J. Res. Appl.(Volume – 5, Issue – 17, Page No’s: 709-713)
DOI:https://zenodo.org/records/13348264
Received: 17th Jan, 2018; Accepted: 15th Feb, 2018; Published: 26th Mar, 2018
Abstract | Full Paper
Case Study
Related technologies and the role of mobile app development life cycle
K. Malyadri and N. Surya Teja
Int. J. Res. Appl.(Volume – 5, Issue – 17, Page No’s: 714-719)
DOI:https://zenodo.org/records/13348311
Received: 20th Jan, 2018; Accepted: 18th Feb, 2018; Published: 27th Mar, 2018
Abstract | Full Paper
Related technologies and the role of mobile app development life cycle
K. Malyadri and N. Surya Teja
Int. J. Res. Appl.(Volume – 5, Issue – 17, Page No’s: 714-719)
DOI:https://zenodo.org/records/13348311
Received: 20th Jan, 2018; Accepted: 18th Feb, 2018; Published: 27th Mar, 2018
Abstract | Full Paper

